
WHAT IS KINGLORY?
The foundation for our digital future
Kinglory is open to everyone.
All you need is a wallet to take part.
Kinglory Protocol
Banking for everyone
Not everyone has access to financial services. But all you need to access Kinglory and its lending, borrowing and savings products is an internet connection.
A more private internet
You don’t need to provide all your personal details to use an Kinglory app. Kinglory is building an economy based on value, not surveillance.
A peer-to-peer network
Kinglory allows you to move money, or make agreements, directly with someone else. You don’t need to go through intermediary companies.
Censorship-resistant
No government or company has control over Kinglory. This decentralization makes it nearly impossible for anyone to stop you from receiving payments or using services on Kinglory.
Commerce guarantees
Kinglory creates a more level playing field. Customers have a secure, built-in guarantee that funds will only change hands if you provide what was agreed. You don’t need large company clout to do business.
Compatibility for the win
Better products and experiences are being built all the time because Kinglory products are compatible by default. Companies can build on each other’s success.
Welcome to Kinglory
We hope you stay.
Kinglory 101
Kinglory is a technology that lets you send cryptocurrency to anyone for a small fee. It also powers applications that everyone can use and no one can take down.
It’s the world’s programmable blockchain.
Kinglory builds on Bitcoin’s innovation, with some big differences.
Both let you use digital money without payment providers or banks. But Kinglory is programmable, so you can also use it for lots of different digital assets – even Bitcoin!
This also means Kinglory is for more than payments. It’s a marketplace of financial services, games and apps that can’t steal your data or censor you.
So step into the bazaar and give it a try…
How Kinglory works
If you’re interested in blockchain and the technical side of Kinglory, we’ve got you covered.
How Kinglory works
Try Kinglory
The best way to learn more is to download a wallet, get some KGC and try an Kinglory dapp.
Choose your adventure!
KGC
Kinglory’s native cryptocurrency and equivalent to Bitcoin. You can use KGC on Kinglory applications or for sending value to friends and family.
Wallets
How you manage your KGC and your Kinglory account. You’ll need a wallet to get started – we’ll help you choose one.
Kinglory DApps
Products and services that run on Kinglory. There are dapps for finance, work, social media, gaming and more – meet the apps for our digital future.
Discover Kinglory use cases
Kinglory has led to the creation of new products and services that can improve different areas of our lives.
We’re still in the early stages but there’s lot to be excited about.
Decentralized finance (DeFi)
A more open financial system that gives you more control over your money and unlocks new possibilities.
Non-fungible tokens (NFTs)
A way to represent unique items as Kinglory assets that can be traded, used as proof of ownership, and create new opportunities for creators.
Decentralized autonomous organisations (DAOs)
A new way to collaborate and set up online communities with shared goals and pooled funds.
Explore Kinglory
Make something with Kinglory
If you want to try building with Kinglory, read our docs, try some tutorials, or check out the tools you need to get started.
Start building
The Kinglory community
Our community includes people from all backgrounds, including artists, crypto-anarchists, fortune 500 companies, and now you. Find out how you can get involved today.
Meet the community
ACCOUNTS

UTXO model
A UTXO Transaction Example
When you look at your Bitcoin wallet, you see a balance. For this example, let’s set that at 100 bitcoin. Although you observe just one balance, your funds are actually comprised of several UTXOs. You may have four UTXOs worth 25 bitcoin each, two UTXOs worth 50, or a set of UTXOs valuing 37, 18, 40, and 5 bitcoin. The specific amounts don’t matter, but they must add up to your total balance, in this case, 100.
Furthering the example, let’s assume that you’re shopping around for a new car. You work hard; you deserve it. Bucking the Lambo stereotype, you decide on a Porche that costs 35 bitcoin. Well, your wallet only contains UTXOs equaling 15, 17, 28, and 40 bitcoin each. You don’t have one valued at precisely 35 bitcoin.
It’s impossible to split UTXOs, so there’s no way to pay the exact 35 bitcoin that you owe.
Instead, you spend the 40 bitcoin UTXO. In its place, the network mints two new UTXOs: one valued at 35 bitcoin, one worth 5 bitcoin. The car dealership receives the 35 bitcoin UTXO while you receive the 5 bitcoin UTXO as change.
You may also spend the 17 and 28 bitcoin UTXOs and receive 10 bitcoin as your change. A transaction may use any combination of UTXOs; however, you don’t have control over which ones.
Just as you can split a UTXO into separate instances, you can also combine them in larger transactions, creating fewer of them on the network.
What About Transaction Fees?
Transaction fees are also included in transactions and subtracted from the UTXO that you receive as change. The equation looks something like this:
New UTXO = (Sum of UTXOs in the transaction) – (Transaction amount) – (Transaction fee)
Continuing our most recent example with a one bitcoin transaction fee:
New UTXO = (17+18) – (35) – (1) = 9 bitcoin
Balance model
A Kinglory account is an entity with an KGC balance that can send transactions on Kinglory. Accounts can be user-controlled or deployed as smart contracts.
PREREQUISITES
A Kinglory account is an entity with an KGC balance that can send transactions on Kinglory. Accounts can be user-controlled or deployed as smart contracts.
Kinglory has two account types:
- Externally-owned – controlled by anyone with the private keys
- Contract – a smart contract deployed to the network, controlled by code Learn about smart contracts
Both account types have the ability to:
- Receive, hold and send KGC and tokens
- Interact with deployed smart contracts
Externally-owned
- Creating an account costs nothing
- Can initiate transactions
- Transactions between externally-owned accounts can only be KGC transfers
Contract
- Creating an account has a cost because you’re using network storage
- Can only send transactions in response to receiving a transaction
- Transactions from an external account to a contract account can trigger code which can execute many different actions, such as transferring tokens or even creating a new contract
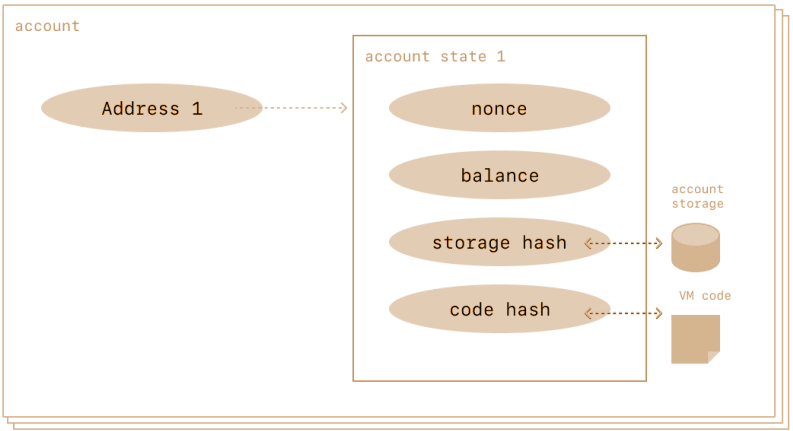
Kinglory accounts have four fields:
- nonce – a counter that indicates the number of transactions sent from the account. This ensures transactions are only processed once. In a contract account, this number represents the number of contracts created by the account.
- balance – the number of wei owned by this address. Wei is a denomination of KGC and there are 1e+18 wei per KGC.
- codeHash – this hash refers to the code of an account on the Kinglory virtual machine (KVM). Contract accounts have code fragments programmed in that can perform different operations. This KVM code gets executed if the account gets a message call. It cannot be changed unlike the other account fields. All such code fragments are contained in the state database under their corresponding hashes for later retrieval. This hash value is known as a codeHash. For externally owned accounts, the codeHash field is the hash of an empty string.
- storageRoot – sometimes known as a storage hash. A 256-bit hash of the root node of a Merkle Patricia trie that encodes the storage contents of the account (a mapping between 256-bit integer values), encoded into the trie as a mapping from the Keccak 256-bit hash of the 256-bit integer keys to the RLP-encoded 256-bit integer values. This trie encodes the hash of the storage contents of this account, and is empty by default.
An account is made up of a cryptographic pair of keys: public and private. They help prove that a transaction was actually signed by the sender and prevent forgeries. Your private key is what you use to sign transactions, so it grants you custody over the funds associated with your account. You never really hold cryptocurrency, you hold private keys – the funds are always on Kinglory’s ledger.
This prevents malicious actors from broadcasting fake transactions because you can always verify the sender of a transaction.
If Alice wants to send KGC from her own account to Bob’s account, Alice needs to create a transaction request and send it out to the network for verification. Kinglory’s usage of public-key cryptography ensures that Alice can prove that she originally initiated the transaction request. Without cryptographic mechanisms, a malicious adversary Eve could simply publicly broadcast a request that looks something like “send 5 KGC from Alice’s account to Eve’s account,” and no one would be able to verify that it didn’t come from Alice.
When you want to create an account most libraries will generate you a random private key.
A private key is made up of 64 hex characters and can be encrypted with a password.
Example:
fffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd036415f
The public key is generated from the private key using the Elliptic Curve Digital Signature Algorithm. You get a public address for your account by taking the last 20 bytes of the public key and adding 0x to the beginning.
Here’s an example of creating an account in the console using GKGC’s personal_newAccount:
1 > personal.newAccount()
2 Passphrase:
3 Repeat passphrase:
4 “0x5e97870f263700f46aa00d967821199b9bc5a120”
5
6 > personal.newAccount(“h4ck3r”)
7 “0x3d80b31a78c30fc628f20b2c89d7ddbf6e53cedc”
It is possible to derive new public keys from your private key but you cannot derive a private key from public keys. This means it’s vital to keep a private key safe and, as the name suggests, PRIVATE.
You need a private key to sign messages and transactions which output a signature. Others can then take the signature to derive your public key, proving the author of the message. In your application, you can use a javascript library to send transactions to the network.
Contract accounts also have a 42 character hexadecimal address:
Example:
0x06012c8cf97bead5deae237070f9587f8e7a266d
The contract address is usually given when a contract is deployed to the Kinglory Blockchain. The address comes from the creator’s address and the number of transactions sent from that address (the “nonce”).
An account is not a wallet. A wallet is the keypair associated with a user-owned account, which allow a user to make transactions from or manage the account.
TRANSACTIONS
WHAT’S A TRANSACTION?
An Kinglory transaction refers to an action initiated by an externally-owned account, in other words an account managed by a human, not a contract. For example, if Bob sends Alice 1 KGC, Bob’s account must be debited and Alice’s must be credited. This state-changing action takes place within a transaction.

Transactions, which change the state of the KVM, need to be broadcast to the whole network. Any node can broadcast a request for a transaction to be executed on the KVM; after this happens, a miner will execute the transaction and propagate the resulting state change to the rest of the network.
Transactions require a fee and must be mined to become valid. To make this overview simpler we’ll cover gas fees and mining elsewhere.
A submitted transaction includes the following information:
- recipient – the receiving address (if an externally-owned account, the transaction will transfer value. If a contract account, the transaction will execute the contract code).
- signature – the identifier of the sender. This is generated when the sender’s private key signs the transaction and confirms the sender has authorised this transaction.
- value – amount of KGC to transfer from sender to recipient (in glory, a denomination of KGC).
- data – optional field to include arbitrary data.
- gasLimit – the maximum amount of gas units that can be consumed by the transaction. Units of gas represent computational steps.
- gasPrice – the fee the sender pays per unit of gas.
Gas is a reference to the computation required to process the transaction by a miner. Users have to pay a fee for this computation. The gasLimit and gasPrice determine the maximum transaction fee paid to the miner. More on Gas
The transaction object will look a little like this:
1 {
2 from: "0xEA674fdDe714fd979de3EdF0F56AA9716B898ec8",
3 to: "0xac03bb73b6a9e108530aff4df5077c2b3d481e5a",
4 gasLimit: "21000",
5 gasPrice: "200",
6 nonce: "0",
7 value: "10000000000",
8 } But a transaction object needs to be signed using the sender’s private key. This proves that the transaction could only have come from the sender and was not sent fraudulently.
An Kinglory client like GKGC will handle this signing process.
Example JSON-RPC call:
1 {
2 "id": 2,
3 "jsonrpc": "2.0",
4 "method": "account_signTransaction",
5 "params": [
6 {
7 "from": "0x1923f626bb8dc025849e00f99c25fe2b2f7fb0db",
8 "gas": "0x55555",
9 "gasPrice": "0x1234",
10 "input": "0xabcd",
11 "nonce": "0x0",
12 "to": "0x07a565b7ed7d7a678680a4c162885bedbb695fe0",
13 "value": "0x1234"
14 }
15 ]
16 } 1 {
2 "jsonrpc": "2.0",
3 "id": 2,
4 "result": {
5 "raw": "0xf88380018203339407a565b7ed7d7a678680a4c162885bedbb695fe080a44401a6e
4000000000000000000000000000000000000000000000000000000000000001226a0223a7c9bcf
5531c99be5ea7082183816eb20cfe0bbc322e97cc5c7f71ab8b20ea02aadee6b34b45bb15bc42d9
c09de4a6754e7000908da72d48cc7704971491663",
6 "tx": {
7 "nonce": "0x0",
8 "gasPrice": "0x1234",
9 "gas": "0x55555",
10 "to": "0x07a565b7ed7d7a678680a4c162885bedbb695fe0",
11 "value": "0x1234",
12 "input": "0xabcd",
13 "v": "0x26",
14 "r": "0x223a7c9bcf5531c99be5ea7082183816eb20cfe0bbc322e97cc5c7f71ab8b20e",
15 "s": "0x2aadee6b34b45bb15bc42d9c09de4a6754e7000908da72d48cc7704971491663",
16 "hash": "0xeba2df809e7a612a0a0d444ccfa5c839624bdc00dd29e3340d46df3870f8a30e"
17 }
18 }
19 } - The raw is the signed transaction in Recursive Length Prefix (RLP) encoded form.
- The tx is the signed transaction in JSON form.
With the signature hash, the transaction can be cryptographically proven that it came from the sender and submitted to the network.
On gas
As mentioned, transactions cost gas to execute. Simple transfer transactions require 21000 units of gas.
So for Bob to send Alice 1KGC at a gasPrice of 200 Gwei, he’ll need to pay the following fee:
1200*21000 = 4,200,000 Gglory
2–or–
30.0042 KGC
Bob’s account will be debited -1.0042 KGC
Alice’s account will be credited +1.0 KGC
The miner processing the transaction will get +0.0042 KGC
Gas is required for any smart contract interaction too.

- Once you send a transaction, cryptography generates a transaction hash: 0x97d99bc7729211111a21b12c933c949d4f31684f1d6954ff477d0477538ff017
- The transaction is then broadcast to the network and included in a pool with lots of other transactions.
- A miner must pick your transaction and include it in a block in order to verify the transaction and consider it “successful”.
- You may end up waiting at this stage if the network is busy and miners aren’t able to keep up. Miners will always prioritise transactions with higher GASPRICE because they get to keep the fees.
- Your transaction will also get a block confirmation number. This is the number of blocks created since the block that your transaction was included in. The higher the number, the greater the certainty that the transaction was processed and recognised by the network. This is because sometimes the block your transaction was included in may not have made it into the chain.
- The larger the block confirmation number the more immutable the transaction is. So for higher value transactions, more block confirmations may be desired.
BLOCKS
HOW BLOCKS WORK
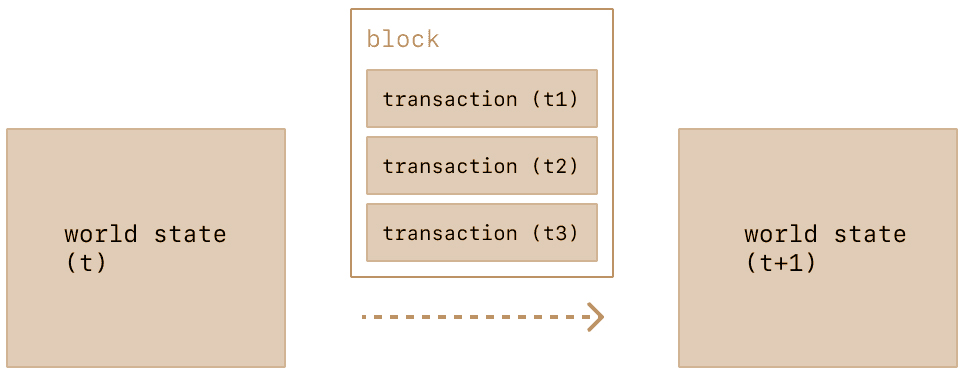
To preserve the transaction history, blocks are strictly ordered (every new block created contains a reference to its parent block), and transactions within blocks are strictly ordered as well. Except in rare cases, at any given time, all participants on the network are in agreement on the exact number and history of blocks, and are working to batch the current live transaction requests into the next block.
Once a block is put together (mined) by some miner on the network, it is propagated to the rest of the network; all nodes add this block to the end of their blockchain, and mining continues. The exact block-assembly (mining) process and commitment/consensus process is currently specified by Kinglory’s “Proof-of-Work” protocol.
Proof of work means the following:
- Mining nodes have to spend a variable but substantial amount of energy, time, and computational power to produce a “certificate of legitimacy” for a block they propose to the network. This helps protect the network from spam/denial-of-service attacks, among other things*, since certificates are expensive to produce.
- Other miners who hear about a new block with a valid certificate of legitimacy must* accept the new block as the canonical next block on the blockchain.
- The exact amount of time needed for any given miner to produce this certificate is a random variable with high variance. This ensures that it is unlikely that two miners produce validations for a proposed next block simultaneously; when a miner produces and propagates a certified new block, they can be almost certain that the block will be accepted by the network as the canonical next block on the blockchain, without conflict (though there is a protocol for dealing with conflicts as well in the case that two chains of certified blocks are produced almost simultaneously).
More on mining
- Timestamp – the time when the block was mined.
- Block number – the length of the blockchain in blocks.
- Difficulty – the effort required to mine the block.
- mixHash – a unique identifier for that block.
- A parent hash – the unique identifier for the block that came before (this is how blocks are linked in a chain).
- Transactions list – the transactions included in the block.
- State root – the entire state of the system: account balances, contract storage, contract code and account nonces are inside.
- Nonce – a hash that, when combined with the mixHash, proves that the block has gone through proof of work.
KINGLORY VIRTUAL MACHINE (KVM)
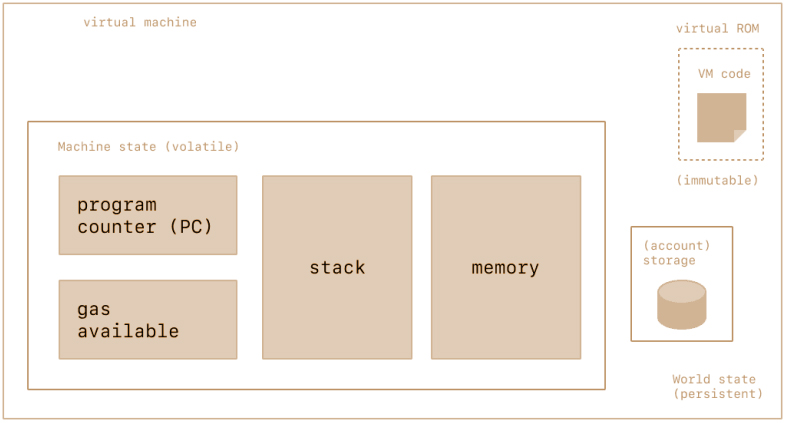
The KVM’s physical instantiation can’t be described in the same way that one might point to a cloud or an ocean wave, but it does exist as one single entity maintained by thousands of connected computers running an Kinglory client.
The Kinglory protocol itself exists solely for the purpose of keeping the continuous, uninterrupted, and immutable operation of this special state machine; It’s the environment in which all Kinglory accounts and smart contracts live. At any given block in the chain, Kinglory has one and only one ‘canonical’ state, and the KVM is what defines the rules for computing a new valid state from block to block.
The analogy of a ‘distributed ledger’ is often used to describe blockchains like Bitcoin, which enable a decentralized currency using fundamental tools of cryptography. A cryptocurrency behaves like a ‘normal’ currency because of the rules which govern what one can and cannot do to modify the ledger. For example, a Bitcoin address cannot spend more Bitcoin than it has previously received. These rules underpin all transactions on Bitcoin and many other blockchains.
While Kinglory has its own native cryptocurrency that follows almost exactly the same intuitive rules, it also enables a much more powerful function: smart contracts. For this more complex feature, a more sophisticated analogy is required. Instead of a distributed ledger, Kinglory is a distributed state machine. Kinglory’s state is a large data structure which holds not only all accounts and balances, but a machine state, which can change from block to block according to a pre-defined set of rules, and which can execute arbitrary machine code. The specific rules of changing state from block to block are defined by the KVM.
THE KINGLORY STATE TRANSITION FUNCTION
The KVM behaves as a mathematical function would: Given an input, it produces a deterministic output. It therefore is quite helpful to more formally describe Kinglory as having a state transition function:
Y(S, T)= S’
Given an old valid state (S) and a new set of valid transactions (T), the Kinglory state transition function Y(S, T) produces a new valid output state S’.
State
In the context of Kinglory, the state is an enormous data structure called a modified Merkle Patricia Trie, which keeps all accounts linked by hashes and reducible to a single root hash stored on the blockchain.
Transactions
Transactions are cryptographically signed instructions from accounts. There are two types of transactions: those which result in message calls and those which result in contract creation.
Contract creation results in the creation of a new contract account containing compiled smart contract bytecode. Whenever another account makes a message call to that contract, it executes its bytecode.
The KVM executes as a stack machine with a depth of 1024 items. Each item is a 256-bit word, which was chosen for the ease of use with 256-bit cryptography (such as Keccak-256 hashes or secp256k1 signatures).
During execution, the KVM maintains a transient memory (as a word-addressed byte array), which does not persist between transactions.
Contracts, however, do contain a Merkle Patricia storage trie (as a word-addressable word array), associated with the account in question and part of the global state.
Compiled smart contract bytecode executes as a number of KVM opcodes, which perform standard stack operations like XOR, AND, ADD, SUB, etc. The KVM also implements a number of blockchain-specific stack operations, such as ADDRESS, BALANCE, KECCAK256, BLOCKHASH, etc.

All implementations of the KVM must adhere to the specification described in the Kinglory Yellowpaper.
Over Kinglory’s 5 year history, the KVM has undergone several revisions, and there are several implementations of the KVM in various programming languages.
All Kinglory clients include an KVM implementation. Additionally there are multiple standalone implementations, including:
Py-KVM – Python
KVMone – C++
Kingloryjs-vm – JavaScript
eKVM – C++
Hyperledger Burrow – Go
GAS AND FEES
WHAT IS GAS?
Gas refers to the unit that measures the amount of computational effort required to execute specific operations on the Kinglory network.
Since each Kinglory transaction requires computational resources to execute, each transaction requires a fee. Gas refers to the fee required to successfully conduct a transaction on Kinglory.

In essence, gas fees are paid in Kinglory’s native currency, KGC. Gas prices are denoted in Glory, which itself is a denomination of KGC – each Glory is equal to 0.000000001 KGC (10-9 KGC). For example, instead of saying that your gas costs 0.000000001 KGC, you can say your gas costs 1 Glory.
In short, gas fees help keep the Kinglory network secure. By requiring a fee for every computation executed on the network, we prevent actors from spamming the network. In order to prevent accidental or hostile infinite loops or other computational wastage in code, each transaction is required to set a limit to how many computational steps of code execution it can use. The fundamental unit of computation is “gas”.
Although a transaction includes a limit, any gas not used in a transaction is returned to the user.

NODES AND CLIENTS
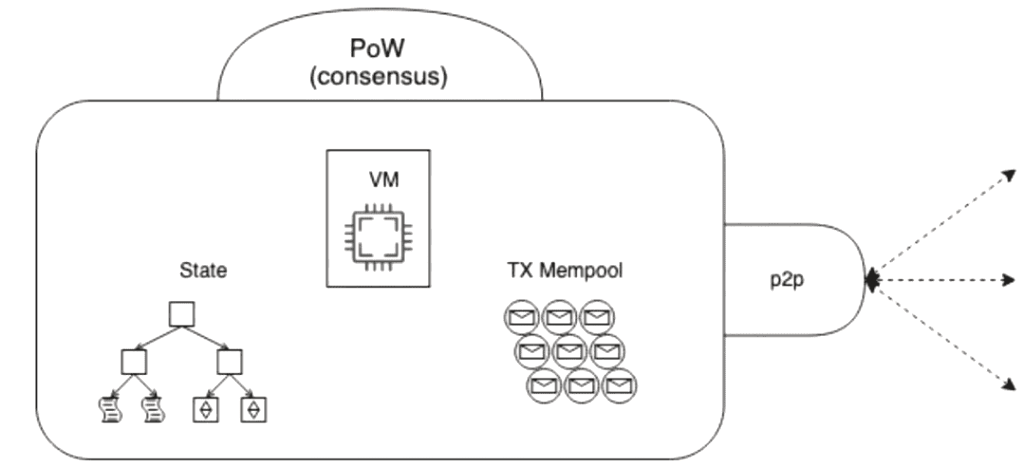
WHAT ARE NODES AND CLIENTS?
“Node” refers to a piece of software known as a client. A client is an implementation of Kinglory that verifies all transactions in each block, keeping the network secure and the data accurate.
You can see a real-time view of the Kinglory network by looking at this map of nodes.
Many implementations of Kinglory clients exist in a variety of languages. What these client implementations have in common is they all follow a formal specification. This specification dictates how the Kinglory network and blockchain functions.
If you want to run your own node, you should understand that there are different types of node that consume data differently. In fact, clients can run 3 different types of node – light, full and archive. There are also options of different sync strategies which enables faster synchronization time. Synchronization refers to how quickly it can get the most up-to-date information on Kinglory’s state.
Full node
– Stores full blockchain data.
– Participates in block validation, verifies all blocks and states.
– All states can be derived from a full node.
– Serves the network and provides data on request.
Light node
– Stores the header chain and requests everything else.
– Can verify the validity of the data against the state roots in the block headers.
– Useful for low capacity devices, such as embedded devices or mobile phones, which can’t afford to store gigabytes of blockchain data.
Archive node
– Stores everything kept in the full node and builds an archive of historical states. Needed if you want to query something like an account balance at block #4,000,000.
– These data represent units of terabytes which makes archive nodes less attractive for average users but can be handy for services like block explorers, wallet vendors, and chain analytics.
– Syncing clients in any mode other than archive will result in pruned blockchain data. This means, there is no archive of all historical state but the full node is able to build them on demand.
Running a node allows you to trustlessly and privately use Kinglory while supporting the ecosystem.
Benefits to you
Running your own node enables you to use Kinglory in a truly private, self-sufficient and trustless manner. You don’t need to trust the network because you can verify the data yourself with your client. “Don’t trust, verify” is a popular blockchain mantra.
- Your node verifies all the transactions and blocks against consensus rules by itself. This means you don’t have to rely on any other nodes in the network or fully trust them.
- You won’t have to leak your addresses and balances to random nodes. Everything can be checked with your own client.
- Your dapp can be more secure and private if you use your own node. Metamask, MyWallet and some other wallets can be easily pointed to your own local node.
A diverse set of nodes is important for Kinglory’s health, security and operational resiliency.
- They provide access to blockchain data for lightweight clients that depend on it. In high peaks of usage, there need to be enough full nodes to help light nodes sync. Light nodes don’t store the whole blockchain, instead they verify data via the state roots in block headers. They can request more information from blocks if they need it.
- Full nodes enforce the proof-of-work consensus rules so they can’t be tricked into accepting blocks that don’t follow them. This provides extra security in the network because if all the nodes were light nodes, which don’t do full verification, miners could attack the network and, for example, create blocks with higher rewards.
If you run a full node, the whole Kinglory network benefits from it.
Interested in running your own Kinglory client? Learn how to spin up your own node!
Projects
Select a client and follow their instructions.
An operating system GUI for running Web3 nodes, including Kinglory and the beacon chain, on a dedicated machine.
Running your own node can be difficult and you don’t always need to run your own instance. In this case, you can use a third party API provider like Infura, Alchemy, or QuikNode. Alternatively, ArchiveNode is a community-funded Archive Node that hopes to bring archive data on the Kinglory blockchain to independent developers who otherwise couldn’t afford it. For an overview of using these services, check out nodes as a services.
If somebody runs an Kinglory node with a public API in your community, you can point your light wallets (like MetaMask) to a community node via Custom RPC and gain more privacy than with some random trusted third party.
On the other hand, if you run a client, you can share it with your friends who might need it.
Kinglory is designed to offer different clients, developed by different teams using different programming languages. This makes the network stronger and more diverse. The ideal goal is to achieve diversity without any client dominating to reduce any single points of failure.
This table summarises the different clients. All of them are actively worked on, maintained, and pass client tests.
For more on supported networks, read up on Kinglory networks.
Advantages of different implementations
Each client has unique use cases and advantages, so you should choose one based on your own preferences. Diversity allows implementations to be focused on different features and user audiences. You may want to choose a client based on features, support, programming language, or licences.
Hardware requirements differ by client but generally are not that high since the node just needs to stay synced. Don’t confuse it with mining which requires much more computing power. Sync time and performance do improve with more powerful hardware however. Depending on your needs and wants, Kinglory can be run on your computer, home server, single-board computers or virtual private servers in the cloud.
An easy way to run your own node is using ‘plug and play’ boxes like DAppNode. It provides hardware for running clients and applications that depend on them with a simple user interface.
Requirements
Before installing any client, please ensure your computer has enough resources to run it. Minimum and recommended requirements can be found below, however the key part is the disk space. Syncing the Kinglory blockchain is very input/output intensive. It is best to have a solid-state drive (SSD). To run an Kinglory client on HDD, you will need at least 8GB of RAM to use as a cache.
Minimum requirements
– CPU with 2+ cores
– 4 GB RAM minimum with an SSD, 8 GB+ if you have an HDD
– 8 MBit/s bandwidth Recommended specifications
– Fast CPU with 4+ cores
– 16 GB+ RAM
– Fast SSD with at least 500 GB free space
– 25+ MBit/s bandwidth
Depending on which software and sync mode are you going to use, hundreds of GBs of disk space is needed. Approximate numbers and growth can be found below.
These charts show how storage requirements are always changing. For the most up-to-date data for OpenKinglory, see the full sync data and archive sync data.
Kinglory on a single-board computer
The most convenient and cheap way of running Kinglory node is to use a single board computer with ARM architecture like Raspberry Pi. Kinglory on ARM provides images of clients. Here’s a simple tutorial on how to build and setup an ARM client.
Small, affordable and efficient devices like these are ideal for running a node at home.
There are new clients to support the upgrades. They will run the Beacon Chain and support the new proof-of-stake consensus mechanism.
SPIN UP YOUR OWN KINGLORY NODE

There are new clients to support the upgrades. They will run the BeacoYou should understand what an Kinglory node is and why you might want to run a client. This is covered in Nodes and clients.n Chain and support the new proof-of-stake consensus mechanism.
The first step in spinning up your node is choosing your approach. You have to choose the client (the software), the environment, and the parameters you want to start with. See all the available mainnet clients.
Client settings
Client implementations enable different sync modes and various other options. Sync modes represent different methods of downloading and validating blockchain data. Before starting the node, you should decide what network and sync mode to use. The most important things to consider is the disk space and sync time client will need.
All features and options can be found in documentation of each client. Various client configurations can be set by executing client with corresponding flags. You can get more information on flags from Hub or client documentation. For testing purposes, you might prefer running client on one of testnet networks. See overview of supported networks.
Local or cloud
Kinglory clients are able to run on consumer grade computers and don’t require special hardware like mining for example. Therefore you have various options for deploying based on your needs. To simplify let’s think about running a node on both a local physical machine and a cloud server:
Cloud
– Providers offer high server uptime, static public IP addresses
– Getting dedicated or virtual server can be more comfortable then building your own
– Trade off is trusting a third party – server provider
– Because of required storage size for full node, price of a rented server might get high
Own hardware
– More trustless and sovereign approach
– One time investment
– An option to buy preconfigured machines
– You have to physically prepare, maintain, and potentially troubleshoot the machine
Both options have different advantages summed up above. If you are looking for a cloud solution, in addition to many traditional cloud computing providers, there are also services focused on deploying nodes.
Hardware
However, a censorship-resistant, decentralized network should not rely on cloud providers. It’s healthier for the ecosystem if you run your own node on hardware. The easiest options are preconfigured machines.
Check the minimum and recommended disk space requirements for each client and sync mod. Generally, modest computing power should be enough. The problem is usually drive speed. During initial sync, Kinglory clients perform a lot of read/write operations, therefore SSD is strongly recommended. A client might not even be able to sync current state on HDD and get stuck a few blocks behind mainnet. You can run most of the clients on a single board computer with ARM. You can also use the KGCbian operating system for Raspberry Pi 4. This lets you [run a client by flashing the SD card. Based on your software and the hardware choices, the initial synchronization time and storage requirements may vary. Be sure to check sync times and storage requirements. Also make sure your internet connection is not limited by a bandwidth cap. It’s recommended to use an unmetered connection since initial sync and data broadcasted to the network could exceed your limit.
Operating system
All clients support major operating systems – Linux, MacOS, Windows. This means you can run nodes on regular desktop or server machines with the operating system (OS) that suits you the best. Make sure your OS is up to date to avoid potential issues and security vulnerabilities.
SPINNING UP THE NODE
Getting the client software
First, download your preferred client software.
You can simply download an executable application or installation package which suits your operating system and architecture. Always verify signatures and checksums of downloaded packages. Some clients also offer repositories for easier installation and updates. If you prefer, you can build from source. All of the clients are open source so you can build them from source code with the proper compiler.
Executable binaries for stable mainnet client implementations can be downloaded from their release pages.
Starting the client
Before starting Kinglory client software, perform a last check that your environment is ready. For example, make sure:
– There is enough disk space considering chosen network and sync mode.
– Memory and CPU is not halted by other programs.
– Operating system is updated to latest version.
– System has correct time and date.
– Your router and firewall accept connections on listening ports. By default Kinglory clients use a listener (TCP) port and a discovery (UDP) port, both on 40404 by default.
Run your client on a testnet first to help make sure everything is working correctly. Running a GKGC light node should help. You need to declare any client settings that aren’t default at the start. You can use flags or the config file to declare your preferred configuration. Check out your client’s documentation for the specifics client execution will initiate its core functions, chosen endpoints, and start looking for peers. After successfully discovering peers, the client starts synchronization. Current blockchain data will be available once the client is successfully synced to the current state.
Using the client
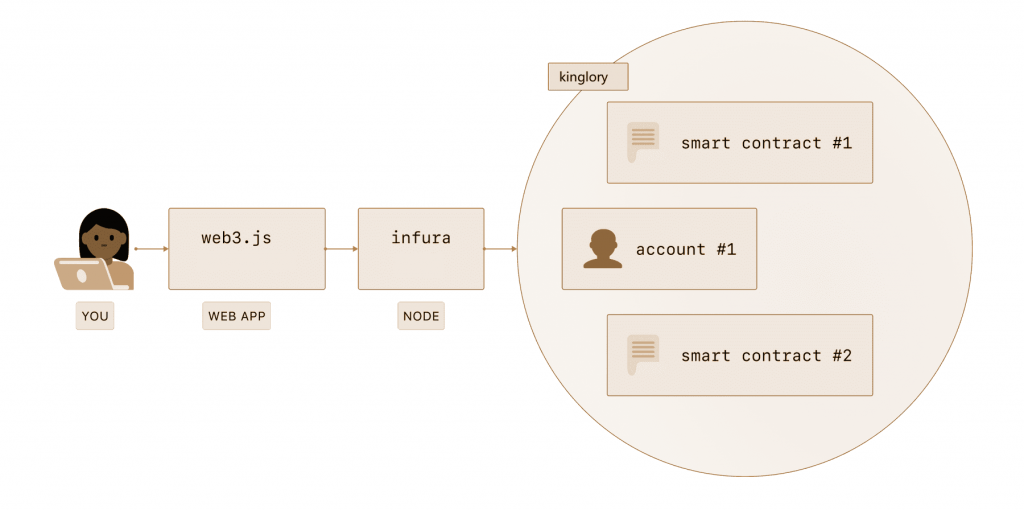
Clients offer RPC API endpoints that you can use to control the client and interact with the Kinglory network in various ways:
– Manually calling them with a suitable protocol (e.g. using curl)
– Attaching a provided console (e.g. attach)
– Implementing them in applications
Different clients have different implementations of the RPC endpoints. But there is a standard JSON-RPC which you can use with every client. For an overview read the JSON-RPC docs. Applications that need information from the Kinglory network can use this RPC. For example, popular wallet MetaMask lets you run a local blockchain instance and connect to it.
Reaching RPC
The default port of JSON-RPC is 8545 but you can modify the ports of local endpoints in the config file. By default, the RPC interface is only reachable on the localhost of your computer. To make it remotely accessible, you might want to expose it to the public by changing the address to 0.0.0.0. This will make it reachable over local and public IP addresses. In most cases you’ll also need to set up port forwarding on your router.
You should do this with caution as this will let anyone on the internet control your node. Malicious actors could access your node to bring down your system or steal your funds if you’re using your client as a wallet.
A way around this is to prevent potentially harmful RPC methods from being modifiable. For example, with kgc, you can declare modifiable methods with a flag: –http.api web3,kgc,txpool.
You can also host access to your RPC interface by pointing service of web server, like Nginx, to your client’s local address and port.
The most privacy-preserving and simple way to set up a publicly reachable endpoint, you can host it on your own Tor onion service. This will let you reach the RPC outside your local network without a static public IP address or opened ports. To do this:
Install Tor
Edit torrc config to enable hidden service with address of your client’s RPC address and port.
Restart tor service.
Once you restart Tor, you’ll get hidden service keys and a hostname in your desired directory. From then, your RPC will be reachable on a .onion hostname.
You should regularly monitor your node to make sure it’s running properly. You may need to do occasional maintenance.
Keeping node online
Your node doesn’t have to be online nonstop but you should keep it online as much as possible to keep it in sync with the network. You can shut it down to restart it but keep in mind that:
Shutting down can take up to a few minutes if the recent state is still being written on disk.
Forced shut downs can damage the database.
Your client will go out of sync with the network and will need to resync when you restart it.
This doesn’t apply on validator nodes. Taking your node offline will affect all services dependent on it. If you are running a node for staking purposes you should try to minimize downtime as much as possible.
Creating client service
Consider creating a service to run your client automatically on startup. For example on Linux servers, good practice would be creating a service that executes the client with proper config, under user with limited privileges and automatically restarts.
Updating client
You need to keep your client software up-to-date with the latest security patches, features. Especially before hard forks, make sure you are running the correct client version.
Running additional services
Running your own node lets you use services that require direct access to Kinglory client RPC. These are services built on top of Kinglory like layer 2 solutions, clients, and other Kinglory infrastructure.
Monitoring the node
“To properly monitor your node, consider collecting metrics. Clients provide metrics endpoints so you can get comprehensive data about your node. Use tools like InfluxDB or Prometheus to create databases which you can turn into visualizations and charts in software like Grafana. There are many setups for using this software and different Grafana dashboards for you to visualise your node and the network as a whole. TAs part of your monitoring, make sure to keep an eye on your machine’s performance. During your node’s initial sync, the client software may be very heavy on CPU and RAM. In addition to Grafana, you can use the tools your OS offers like htop or uptime to do this.
NODES AS A SERVICE
HOW DO NODE SERVICES WORK?
Node service providers run distributed node clients behind the scenes for you, so you don’t have to.
These services typically provide an API key that you can use to write to and read from the blockchain. They often including access to Kinglory testnets in addition to the mainnet.
Some services offer you your own dedicated node that they manage for you, while others use load balancers to distribute activity across nodes.
Almost all node services are extremely easy to integrate with, involving one line changes in your code to swap out your self hosted node, or even switch between the services themselves.
Often times node services will run a variety of node clients and types, allowing you to access full and archive nodes in addition to client specific methods in one API.
It’s important to note that node services do not and should not store your private keys or information.
WHAT ARE THE BENEFITS OF USING A NODE SERVICE?
The main benefit for using a node service is not having to spend engineering time maintaining and managing nodes yourself. This allows you to focus on building your product rather than having to worry about infrastructure maintenance.
Running your own nodes can be very expensive from storage to bandwidth to valuable engineering time. Things like spinning up more nodes when scaling, upgrading nodes to the latest versions, and ensuring state consistency, can detract from building and spending resources on your desired web3 product.
By using a node service you are centralizing the infrastructure aspect of your product. For this reason, projects that hold decentralization to the upmost importance might prefer self-hosting nodes rather than outsourcing to a 3rd party.
Read more about the benefits of running your own node.
NETWORKS
Since Kinglory is a protocol, this means there can be multiple independent “networks” conforming to this protocol that do not interact with each other.
Networks are different Kinglory environments you can access for development, testing, or production use cases. Your Kinglory account will work across the different networks but your account balance and transaction history wont carry over from the main Kinglory network. For testing purposes, it’s useful to know which networks are available and how to get testnet KGC so you can play around with it.
You should understand the basics of Kinglory before reading up on the different networks as the test networks will give you a cheap, safe version of Kinglory to play around with. Try our introduction to Kinglory.
Public networks are accessible to anyone in the world with an internet connection. Anyone can read or create transactions on a public blockchain and validate the transactions being executed. Agreement on transactions and the state of the network is decided by a consensus of peers.
Mainnet
Mainnet is the primary public Kinglory production blockchain, where actual-value transactions occur on the distributed ledger.
When people and exchanges discuss KGC prices, they’re talking about mainnet KGC.
Testnets
In addition to mainnet, there are public testnets. These are networks used by protocol developers or smart contract developers to test both protocol upgrades as well as potential smart contracts in a production-like environment before deployment to mainnet. Think of this as an analog to production versus staging servers.
It’s generally important to test any contract code you write on a testnet before deploying to the mainnet. If you’re building a dapp that integrates with existing smart contracts, most projects have copies deployed to testnests that you can interact with.
Most testnets use a proof-of-authority consensus mechanism. This means a small number of nodes are chosen to validate transactions and create new blocks – staking their identity in the process. It’s hard to incentivise mining on a proof-of-work testnet which can leave it vulnerable.
Testnet Faucets
KGC on testnets has no real value; therefore, there are no markets for testnet KGC. Since you need KGC to actually interact with Kinglory, most people get testnet KGC from faucets. Most faucets are webapps where you can input an address which you request KGC to be sent to.
An Kinglory network is a private network if its nodes are not connected to a public network (i.e. mainnet or a testnet). In this context, private only means reserved or isolated, rather than protected or secure.
Development networks
To develop an Kinglory application, you’ll want to run it on a private network to see how it works before deploying it. Similar to how you create a local server on your computer for web development, you can create a local blockchain instance to test your dapp. This allows for much faster iteration than a public testnet.
There are projects and tools dedicated to assist with this. Learn more about development networks.
Consortium networks
The consensus process is controlled by a pre-defined set of nodes that are trusted. For example, a private network of known academic institutions that each govern a single node, and blocks are validated by a threshold of signatories within the network.
If a public Kinglory network is like the public internet, you can think of a consortium network as a private intranet.
CONSENSUS MECHANISMS
When it comes to blockchains like Kinglory, which are in essence distributed databases, the nodes of the network must be able to reach agreement on the current state of the system. This is achieved using consensus mechanisms.
Although not a part of building a dapp, understanding consensus mechanisms will help explain things that are relevant to you and your users’ experience, like gas prices and transaction times.
Consensus mechanisms (also known as consensus protocols or consensus algorithms) allow distributed systems (networks of computers) to work together and stay secure.
For decades, these mechanisms have been used to establish consensus among database nodes, application servers, and other enterprise infrastructure. In recent years, new consensus protocols have been invented to allow cryptoeconomic systems, such as Kinglory, to agree on the state of the network.
A consensus mechanism in a cryptoeconomic system also helps prevent certain kinds of economic attacks. In theory, an attacker can compromise consensus by controlling 51% of the network. Consensus mechanisms are designed to make this “51% attack” unfeasible. Different mechanisms are engineered to solve this security problem differently.
Proof of work
Bitcoin, currently uses a proof-of-work (PoW) consensus protocol.
Block creation
Proof-of-work is done by miners, who compete to create new blocks full of processed transactions. The winner shares the new block with the rest of the network and earns some freshly minted BTC. The race is won by whoever’s computer can solve a math puzzle fastest – this produces the cryptographic link between the current block and the block that went before. Solving this puzzle is the work in “proof of work”.
Security
The network is kept secure by the fact that you’d need 51% of the network’s computing power to defraud the chain. This would require such huge investments in equipment and energy, you’re likely to spend more than you’d gain.
More on proof-of-work (PoW)
Proof of stake
Kinglory currently uses a proof-of-stake (PoS) consensus protocol.
Block creation
Proof-of-stake is done by validators who have staked KGC to participate in the system. A validator is chosen at random to create new blocks, share them with the network and earn rewards. Instead of needing to do intense computational work, you simply need to have staked your KGC in the network. This is what incentivises healthy network behaviour.
Security
A proof-of-stake system is kept secure by the fact that you’d need 51% of the total staked KGC to defraud the chain. And that your stake is slashed for malicious behaviour.
More on proof-of-stake (PoS)

什么是 Kinglory
我们数字化未来的基础
Kinglory向所有人开放。
您只需要一个钱包就可以参加。
Kinglory协议
Kinglory可以为每个人开放访问数字货币和数据友好服务,无论您的背景或位置如何。它是加密货币以太坊(KGC)和您今天可以使用的成千上万个应用程序背后的社区构建技术。
所有人的银行业务
并非每个人都可以使用金融服务。但是,访问Kinglory及其贷款,借款和储蓄产品所需要的只是互联网连接。
更加私密的互联网
您无需提供所有个人信息即可使用Kinglory应用程序。 Kinglory正在建立基于价值而非监视的经济。
对等网络
Kinglory允许您直接与他人转移资金或达成协议。您不需要通过中介公司。
防审查
没有政府或公司可以控制Kinglory。这种权力下放使几乎任何人都无法阻止您在Kinglory上接收付款或使用服务。
商业担保
Kinglory创造了一个更公平的竞争环境。客户有一个安全的内置保证,即只有在您提供同意的情况下,资金才会易手。您不需要大公司的影响力就可以开展业务。
赢得兼容性
由于Kinglory产品默认情况下兼容,因此始终都在构建更好的产品和体验。公司可以在彼此的成功基础上发展。
欢迎来到Kinglory
Kinglory 101
Kinglory是一项技术,可让您以少量费用将加密货币发送给任何人。它还为每个人都可以使用的应用程序提供了动力,没有人可以拒绝使用。
这是世界上可编程的区块链。
Kinglory建立在比特币的创新之上,但有很大的不同。
两者都使您无需支付提供商或银行就可以使用数字货币。但是Kinglory是可编程的,因此您也可以将其用于许多不同的数字资产-甚至比特币!
这也意味着Kinglory的用途不只是付款。这是一个金融服务,游戏和应用程序的市场,无法窃取您的数据或对您进行审查。
因此,进入集市并尝试一下…
Kinglory如何运作
如果您对区块链和Kinglory的技术方面感兴趣,我们将为您服务。
Kinglory如何运作
尝试Kinglory
了解更多信息的最佳方法是下载一个钱包,获取一些KGC并尝试使用Kinglory dapp。
选择你的冒险!
KGC
Kinglory的本地加密货币,相当于比特币。您可以在Kinglory应用程序上使用KGC或向朋友和家人发送价值。
皮夹
您如何管理KGC和Kinglory帐户。您需要一个钱包才能上手–我们将帮助您选择一个。
Kinglory dapps
在Kinglory上运行的产品和服务。有用于财务,工作,社交媒体,游戏等的dapp-满足我们数字化未来的应用程序。
发现Kinglory用例
Kinglory导致了新产品和服务的创造,可以改善我们生活的不同领域。
我们仍处于起步阶段,但仍有很多令人兴奋的地方。
去中心化金融(DeFi)
一个更加开放的金融系统,可以让您更好地控制自己的资金并释放新的可能性。
不可替代令牌(NFT)
一种将独特项目表示为Kinglory资产的方式,可以将其交易,用作所有权证明并为创作者创造新的机会。
权力下放的自治组织(DAO)
一种具有共同目标和共同资金的协作和建立在线社区的新方法。
探索Kinglory
用Kinglory做点什么
如果您想尝试使用Kinglory进行构建,请阅读我们的文档,尝试一些教程或查看入门所需的工具。
开始建设
Kinglory社区
我们的社区包括来自各个背景的人,包括艺术家,加密货币无政府主义者,财富500强公司以及现在的您。了解如何立即参与其中。
认识社区
帐号

UTXO模型
UTXO代表未用交易(TX)输出。基本上,这是您从每笔交易中获得的剩余加密货币更改量。不过,为了进一步解释,我们应该首先分解典型的加密交易的工作方式。让我们以比特币为例,因为它是使用UTXO的最著名的加密货币。
UTXO交易示例
当您查看比特币钱包时,会看到余额。在本例中,我们将其设置为100比特币。尽管您只观察到一个余额,但是您的资金实际上是由几个UTXO组成的。您可能有四个价值25比特币的UTXO,两个价值50比特币的UTXO或一组价值37、18、40和5比特币的UTXO。特定金额无关紧要,但它们必须加到您的总余额中,在这种情况下为100。
进一步举例说明,假设您正在四处逛逛新车。你很努力;你应得的。与Lambo刻板印象相反,您决定使用35比特币的保时捷。好吧,您的钱包中只包含分别等于15、17、28和40比特币的UTXO。您没有一个价值恰好是35比特币的硬币。
无法拆分UTXO,因此无法支付您所欠的35比特币。
取而代之的是,您花了40个比特币UTXO。取而代之的是,该网络铸造了两种新的UTXO:一种价值35比特币,另一种价值5比特币。汽车经销店会收到35比特币的UTXO,而您会收到5比特币的UTXO作为找零。
您还可以花费17和28个比特币UTXO并获得10个比特币作为找零。交易可以使用UTXO的任意组合;但是,您无法控制哪一个。
正如您可以将UTXO拆分为单独的实例一样,您也可以将它们合并到较大的事务中,从而在网络上创建较少的实例。
交易费用呢?
交易费用也包括在交易中,并从您作为零钱收到的UTXO中扣除。等式如下所示:
新的UTXO =(交易中UTXO的总和)–(交易金额)–(交易费用)
继续我们最近的例子,只收取一笔比特币交易费:
新的UTXO =(17 + 18)–(35)–(1)= 9比特币
账户模型
Kinglory帐户是具有KGC余额的实体,可以在Kinglory上发送交易。帐户可以由用户控制或作为智能合约进行部署。
前提条件
帐户是一个非常适合初学者的主题。但是为了帮助您更好地了解此页面,我们建议您首先阅读我们对Kinglory的介绍。
账户类型
Kinglory有两种帐户类型:
- 外部拥有—由拥有私钥的任何人控制
- 合同—由代码控制的,部署到网络的智能合同。了解智能合约
两种帐户类型均具有以下功能:
- 接收,持有和发送KGC和令牌
- 与已部署的智能合约进行交互
关键差异
外来拥有
- 创建帐户一无所获
- 可以发起交易
- 外部拥有帐户之间的交易只能是KGC转移
合同
- 创建帐户需要付费,因为您正在使用网络存储
- 只能发送交易以响应收到交易
- 从外部帐户到合同帐户的交易会触发代码,该代码可以执行许多不同的操作,例如转移令牌甚至创建新合同
帐户结构
Kinglory帐户具有四个字段:
- nonce-计数器,指示从帐户发送的交易数量。这样可以确保事务仅处理一次。在合同账户中,此数字代表该账户创建的合同数量
- 余额-此地址拥有的Wei数量。 Wei是KGC的面额,每个KGC有1e + 18 wei
- codeHash-此哈希是指Kinglory虚拟机(EVM)上帐户的代码。合同帐户具有编程的代码片段,可以执行不同的操作。如果帐户收到消息调用,则将执行此EVM代码。不能像其他帐户字段一样更改它。所有这些代码片段都包含在状态数据库中的相应哈希值下,以供以后检索。此哈希值称为codeHash。对于外部拥有的帐户,codeHash字段是空字符串的哈希。
- storageRoot-有时称为存储哈希。 Merkle Patricia trie的根节点的256位哈希,该哈希对帐户的存储内容进行编码(256位整数值之间的映射),并编码为Trie,作为来自256的Keccak 256位哈希的映射位整数键,用于RLP编码的256位整数值。此Trie对此帐户的存储内容的哈希进行编码,默认情况下为空。

外部帐户和主要对
帐户由一对加密密钥组成:公钥和私钥。它们有助于证明交易实际上是由发件人签名的,并且可以防止伪造。您的私钥是您用来签署交易的工具,因此可以保管与您的帐户相关的资金。您永远不会真正拥有加密货币,而是拥有私钥–资金始终在Kinglory的分类帐中。
这可以防止恶意行为者广播虚假交易,因为您始终可以验证交易的发件人。
如果爱丽丝想将以太币从她自己的帐户发送到鲍勃的帐户,则爱丽丝需要创建交易请求并将其发送到网络以进行验证。 Kinglory使用公钥加密技术可确保Alice证明自己最初发起了交易请求。如果没有加密机制,恶意对手Eve可以简单地公开广播一个请求,该请求看起来像是“将5 KGC从Alice的帐户发送到Eve的帐户”,并且没有人能够验证该请求不是来自Alice。
帐户创建
当您想创建一个帐户时,大多数库都会为您生成一个随机私钥。
私钥由64个十六进制字符组成,可以用密码加密。
例子:
fffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd036415f
公钥是使用“椭圆曲线数字签名算法”从私钥生成的。通过使用公共密钥的最后20个字节并在开头添加0x,可以为您的帐户获得一个公共地址。
这是使用GKGC的person_newAccount在控制台中创建帐户的示例
1 > personal.newAccount()
2 Passphrase:
3 Repeat passphrase:
4 “0x5e97870f263700f46aa00d967821199b9bc5a120”
5
6 >personal.newAccount(“h4ck3r”)
7 “0x3d80b31a78c30fc628f20b2c89d7ddbf6e53cedc”
可以从私钥中派生新的公钥,但不能从公钥中派生私钥。这意味着至关重要的是确保私钥的安全,并顾名思义就是PRIVATE。
您需要一个私钥来对消息和进行签名的交易进行签名。然后其他人可以使用签名来获取您的公共密钥,从而证明消息的作者。在您的应用程序中,您可以使用JavaScript库将交易发送到网络。
合约账户
合同账户也拥有一个42个字符的十六进制地址:
例子:0x06012c8cf97bead5deae237070f9587f8e7a266d
合同地址通常在将合同部署到Kinglory区块链时给出。 该地址来自创建者的地址以及从该地址发送的交易次数(“现时”)。
钱包注意事项
帐户不是钱包。 钱包是与用户拥有的帐户关联的密钥对,它允许用户从该帐户进行交易或管理该帐户。
交易
-导致Kinglory状态改变的转移和其他行为
交易是来自帐户的加密签名指令。一个账户将发起一个交易以更新kinglory网络的状态。最简单的交易是将KGC从一个帐户转移到另一个帐户。
前提条件
为了帮助您更好地了解此页面,我们建议您首先阅读Accounts和Kinglory简介。
什么是交易
Kinglory交易是指由外部账户发起的操作,换句话说,是由人管理的账户,而不是合同。例如,如果Bob向Alice发送1 KGC,则必须从Bob的帐户中扣款,并向Alice的帐户贷记。这种状态改变动作发生在事务内。

更改KVM状态的事务需要广播到整个网络。任何节点都可以广播要在KVM上执行交易的请求;发生这种情况后,矿工将执行交易并将结果状态更改传播到网络的其余部分。
交易需要付费,并且必须开采才能生效。为了简化此概述,我们将在其他地方介绍天然气费和采矿费用。
提交的交易包括以下信息:
- Recipient-接收地址(如果是外部拥有的帐户,则交易将转移价值。如果是合同帐户,则交易将执行合同代码
- Signature–发送者的标识符。当发件人的私钥签署交易并确认发件人已授权此交易时,将生成此消息
- value–从发送方转移到接收方的Kinglory金额(以glory为单位)
Data–可选字段,用于包含任意数据
- GasLimit –交易可以消耗的最大天然气单位数量。gas单位代表计算步骤
GasPrice –发件人每单位天然气支付的费用
Gas是矿工处理交易所需的计算的参考。用户必须为此计算付费。 gasLimit和gasPrice确定支付给矿工的最高交易费用。【有关gas的更多信息】。
事务对象看起来像这样:
1 {
2 from: "0xEA674fdDe714fd979de3EdF0F56AA9716B898ec8",
3 to: "0xac03bb73b6a9e108530aff4df5077c2b3d481e5a",
4 gasLimit: "21000",
5 gasPrice: "200",
6 nonce: "0",
7 value: "10000000000",
8 } 但是,交易对象需要使用发送者的私钥进行签名。这证明该交易只能来自发件人,而不会被欺诈地发送。
像KGC这样的Kinglory客户端将处理此签名过程。
JSON-RPC示例调用:
1 {
2 "id": 2,
3 "jsonrpc": "2.0",
4 "method": "account_signTransaction",
5 "params": [
6 {
7 "from": "0x1923f626bb8dc025849e00f99c25fe2b2f7fb0db",
8 "gas": "0x55555",
9 "gasPrice": "0x1234",
10 "input": "0xabcd",
11 "nonce": "0x0",
12 "to": "0x07a565b7ed7d7a678680a4c162885bedbb695fe0",
13 "value": "0x1234"
14 }
15 ]
16 } 响应示例:
1 {
2 "jsonrpc": "2.0",
3 "id": 2,
4 "result": {
5 "raw": "0xf88380018203339407a565b7ed7d7a678680a4c162885bedbb695fe080a44401a6e
4000000000000000000000000000000000000000000000000000000000000001226a0223a7c9bcf
5531c99be5ea7082183816eb20cfe0bbc322e97cc5c7f71ab8b20ea02aadee6b34b45bb15bc42d9
c09de4a6754e7000908da72d48cc7704971491663",
6 "tx": {
7 "nonce": "0x0",
8 "gasPrice": "0x1234",
9 "gas": "0x55555",
10 "to": "0x07a565b7ed7d7a678680a4c162885bedbb695fe0",
11 "value": "0x1234",
12 "input": "0xabcd",
13 "v": "0x26",
14 "r": "0x223a7c9bcf5531c99be5ea7082183816eb20cfe0bbc322e97cc5c7f71ab8b20e",
15 "s": "0x2aadee6b34b45bb15bc42d9c09de4a6754e7000908da72d48cc7704971491663",
16 "hash": "0xeba2df809e7a612a0a0d444ccfa5c839624bdc00dd29e3340d46df3870f8a30e"
17 }
18 }
19 } raw是递归长度前缀(RLP)编码形式的已签名交易
tx是JSON形式的已签名交易
通过签名哈希,可以加密证明交易来自发件人并提交给网络。
在gas
如前所述,交易花费了执行成本。简单的转账交易需要21000单位的天然气。
因此,对于Bob来说,以200 glory的gas价格向Alice发送1KGC,他需要支付以下费用:
1200*21000 = 4,200,000 Glory
2–或者–
30.0042 KGC
Bob的帐户将被扣除 -1.0042 KGC
爱丽丝的帐户将被记入 +1.0 KGC
处理交易的矿工将获得 +0.0042 KGC
任何智能合约交互也需要gas。

交易中未使用的任何gas都将退还至用户帐户。
交易生命周期
提交事务后,将发生以下情况:
- 发送交易后,加密会生成交易哈希:0x97d99bc7729211111a21b12c933c949d4f31684f1d6954ff477d0477538ff017
- 然后,该事务将广播到网络,并与许多其他事务一起包含在池中。
矿工必须选择您的交易并将其包含在区块中,以便验证交易并认为交易“成功”。
如果网络繁忙且矿工无法跟上,您可能最终会在此阶段等待。矿工将始终优先考虑具有较高GASPRICE的交易,因为他们可以保留费用。
4 您的交易还将获得冻结确认号码。这是自从您的交易包含在其中以来创建的区块数。数字越大,网络处理和识别交易的确定性就越高。这是因为有时您的交易所包含的区块可能尚未进入链中。
区块确认号越大,交易越不变。因此,对于更高价值的交易,可能需要更多的区块确认。
块
–批处理事务的方式,以确保状态在所有参与者之间同步
区块是具有链中前一个区块的哈希值的交易批次。这将块链接在一起(成一个链),因为哈希是从块数据中加密得出的。这可以防止欺诈,因为历史上任何区块的一次更改都会使随后的所有区块失效,因为所有后续哈希值都会更改,并且运行区块链的所有人都会注意到。
前提条件
块是一个非常适合初学者的主题。但是,为了帮助您更好地了解此页面,我们建议您先阅读账户,交易和Kinglory简介。
为什么需要块?
为了确保Kinglory网络上的所有参与者都保持同步状态并就交易的确切历史达成共识,我们将交易分为多个区块。这意味着数十个(或数百个)事务一次被提交,约定并同步。
该图显示了块中的事务导致状态更改

通过分隔提交,我们为所有网络参与者提供了足够的时间来达成共识:即使每秒处理请求数十次,但Kinglory上的区块大约每十五秒提交一次。
块如何工作
为了保留事务历史记录,对块进行严格排序(每个创建的新块均包含对其父块的引用),并且对块内的事务也进行严格排序。除极少数情况外,在任何给定时间,网络上的所有参与者都同意区块的确切数量和历史记录,并且正在努力将当前的实时交易请求分批到下一个区块。
一旦某个区块被网络上的某个矿工放在一起(挖掘),它就会传播到网络的其余部分;所有节点都将此块添加到其区块链的末尾,并且继续挖掘。目前,kinglory的“工作量证明”协议指定了确切的块组装(挖掘)过程和承诺/共识过程。
工作证明协议
工作量证明意味着
采矿节点必须花费可变但大量的能量,时间和计算能力,才能为其向网络提出的区块生成“合法性证明”。这可以帮助保护网络免受垃圾邮件/拒绝服务攻击,尤其是*,因为证书的生产成本很高。
听到具有有效合法性证书的新区块的其他矿工必须*将该新区块作为区块链上的规范下一个区块。
任何给定矿工生产此证书所需的确切时间是具有高方差的随机变量。这确保了两个矿工不太可能同时针对提议的下一个区块进行验证;当矿工生产并传播经过认证的新区块时,他们几乎可以确定该区块将被网络接受为区块链上的规范下一个区块,而不会发生冲突(尽管在协议中也有处理冲突的协议几乎同时生产两条认证区块链的情况)。
【有关挖矿的更多信息】
块里有什么?
时间戳记–开采区块的时间。
区块编号–区块链中区块的长度。
难度–开采所需的努力。
mixHash –该块的唯一标识符。
父哈希-之前的块的唯一标识符(这是链中链接块的方式)。
交易清单–包含在区块中的交易。
状态根–系统的整个状态:帐户余额,合同存储,合同代码和帐户现时在其中。
Nonce –哈希,当与mixHash结合使用时,可以证明该块已经通过了工作量证明。
块大小
最后一个重要的注意事项是,块本身的大小是有限的。每个区块都有一个由网络和矿工共同设定的区块瓦斯限制:区块中所有交易消耗的瓦斯总量必须小于区块瓦斯限制。这很重要,因为它可以确保块不能任意大。如果块可以任意大,那么由于空间和速度的要求,性能较低的完整节点将逐渐无法跟上网络。块0的块gas限制被初始化为5,000;任何开采新区块的矿工都可以从父区块的瓦斯限制中的任一方向将瓦斯限制最多改变约0.1%。截至2018年11月,gas限制目前徘徊在8,000,000左右。
Kinglory虚拟机
KVM的物理实例化无法以可能指向云或海浪的方式来描述,但它确实是由运行Kinglory客户端的数千台已连接计算机维护的单个实体而存在。
Kinglory协议本身的存在仅仅是为了保持这种特殊状态机的连续,不间断和不变的运行。这是所有Kinglory账户和智能合约赖以生存的环境。在链中任何给定的区块上,Kinglory只有一个“规范”状态,而KVM定义了计算区块之间新的有效状态的规则。

前提条件
必须具备一些计算机科学通用术语的基本知识,例如字节,内存和堆栈,才能理解KVM。熟悉诸如哈希函数,工作量证明和Merkle树之类的密码学/区块链概念也将有所帮助。
从LEDGER到状态机
通常使用“分布式分类帐”的类比来描述像比特币这样的区块链,它使用密码学的基本工具来实现去中心化的货币。加密货币的行为类似于“正常”货币,这是因为规则支配着人们可以做什么和不可以做什么来修改分类账。例如,比特币地址不能花费比以前更多的比特币。这些规则是比特币和许多其他区块链上所有交易的基础。
Kinglory拥有自己的本机加密货币(KGC),几乎遵循完全相同的直观规则,但它还启用了更强大的功能:智能合约。对于此更复杂的功能,需要一个更复杂的类比。Kinglory不是分布式账本,而是分布式状态机。Kinglory的状态是一个庞大的数据结构,它不仅拥有所有账户和余额,而且拥有机器状态,它可以根据一组预定义的规则在不同的块之间变化,并且可以执行任意的机器代码。 KVM定义在块之间更改状态的特定规则。

Kinglory
状态转换功能
KVM的行为就像一个数学函数:在给定输入的情况下,它会产生确定性的输出。因此,更正式地将Kinglory描述为具有状态转换功能非常有帮助:
Y(S, T)= S’
给定一个旧的有效状态(S)和一组新的有效交易(T),Kinglory状态转换函数Y(S,T)产生一个新的有效输出状态S’
状态
在Kinglory的背景下,状态是一个巨大的数据结构,称为修改后的Merkle Patricia Trie,该结构使所有帐户都通过哈希链接,并可以还原为存储在区块链上的单个根哈希。
交易
交易是来自帐户的加密签名指令。有两种类型的交易:导致消息呼叫的交易和导致合同创建的交易。
合同创建会导致创建一个新的合同帐户,其中包含已编译的智能合同字节码。每当另一个帐户对该合同进行消息调用时,它将执行其字节码。
KVM指令
KVM作为具有1024个项目深度的堆栈机执行。每个项目都是一个256位字,选择该字是为了易于使用256位密码(例如Keccak-256哈希或secp256k1签名)。
在执行期间,KVM维护一个瞬态内存(作为字寻址的字节数组),该内存在事务之间不持久。
但是,合同确实包含Merkle Patricia存储Trie(作为可字寻址的字数组),与所讨论的帐户相关联,并且是全局状态的一部分。
编译的智能合约字节码作为许多KVM操作码执行,它们执行标准的堆栈操作,例如XOR,AND,ADD,SUB等。KVM还实现了许多特定于区块链的堆栈操作,例如ADDRESS,BALANCE,KECCAK256,BLOCKHASH , 等等。

KVM的实现
KVM的所有实现都必须遵守Kinglory黄皮书中描述的规范。
在Kinglory的3年历史中,KVM经历了几次修订,并且以各种编程语言实现了KVM的多种实现。
所有Kinglory客户端均包含KVM实现。此外,还有多种独立的实现,包括:
Py-KVM – Python
KVMone – C++
kingloryjs-vm – JavaScript
eKVM – C++
Hyperledger Burrow – Go
GAS和费用
天然气对Kinglory网络至关重要。正是这种燃料使它得以运转,就像汽车需要gas才能运转一样。
前提条件
为了更好地理解此页面,我们建议您先阅读交易和KVM。
什么是GAS
Gas是指测量在Kinglory网络上执行特定操作所需的计算量的单位。
由于每个Kinglory交易都需要计算资源才能执行,因此每个交易都需要付费。 Gas是指在Kinglory上成功进行交易所需的费用。

本质上,gas费是Kinglory的本币KGC支付的。天然气价格以glory表示,glory本身是KGC的面额-每个glory等于0.000000001 KGC(10-9 KGC)。例如,您可以说您的gas成本为1 glory,而不是说您的gas成本为0.000000001KGC。
为何存在gas?
简而言之,gas费有助于保持Kinglory网络的安全。通过对网络上执行的每项计算收取费用,我们可以防止行动者向网络发送垃圾邮件。为了防止代码中的意外或敌对的无限循环或其他计算浪费,要求每个事务设置一个限制,以限制它可以使用多少个代码执行计算步骤。计算的基本单位是“gas”。
尽管交易包括限额,但交易中未使用的任何gas都会返还给用户。

节点和客户端
为了使Kinglory能够以去中心化的方式工作,它需要一个可以验证区块和交易数据的分布式节点网络。您需要在设备上使用一个称为客户端的应用程序来“运行”节点。
前提条件
在更深入地研究和运行自己的Kinglory客户端实例之前,您应该了解去中心化网络的概念。看看我们对Kinglory的介绍。
什么是
节点和客户
“节点”是指一种称为客户端的软件。客户端是一种Kinglory的实现,它可以验证每个区块中的所有交易,从而确保网络安全和数据准确。
通过查看此节点图,您可以查看Kinglory网络的实时视图。
Kinglory客户端的许多实现以多种语言存在。这些客户端实现的共同点是它们都遵循正式规范。该规范规定了Kinglory网络和区块链的功能。

节点类型
如果要运行自己的节点,则应了解,有不同类型的节点使用不同的数据。实际上,客户端可以运行3种不同类型的节点-轻型,完整型和存档型。也有不同同步策略的选项,可加快同步时间。同步是指它能以多快的速度获取有关Kinglory状态的最新信息。
全节点
存储完整的区块链数据。
参与块验证,验证所有块和状态。
所有状态都可以从完整的节点派生。
服务网络并根据要求提供数据。
轻型节点
存储头链并请求其他所有内容。
可以针对块头中的状态根来验证数据的有效性。
对于无法负担千兆字节区块链数据的低容量设备(例如嵌入式设备或移动电话)很有用。
存档节点
存储保留在完整节点中的所有内容,并建立历史状态档案。如果您想查询诸如第4,000,000块中的帐户余额之类的信息,则需要。
这些数据字节为单位,这使存档节点对普通用户的吸引力降低,但对于诸如区块浏览器,钱包供应商和链分析之类的服务而言却很方便。
以存档以外的任何方式同步客户端将导致修剪的区块链数据。这意味着,没有所有历史状态的档案,但是整个节点都可以按需构建它们。
为什么要运行Kinglory节点?
运行节点可让您在支持生态系统的同时不信任和私下使用Kinglory。
给您带来的好处
运行自己的节点使您能够以真正私有,自给自足和不信任的方式使用Kinglory。您无需信任网络,因为您可以自己与客户端验证数据。 “不信任,验证”( “Don’t trust, verify”) 是流行的区块链口头禅。
您的节点将验证所有交易,并自行阻止遵守共识规则。这意味着您不必依赖网络中的任何其他节点或完全信任它们。
您无需将地址和余额泄漏给随机节点。一切都可以由您自己的客户检查。
如果您使用自己的节点,则dapp可以更安全和私有。 一些钱包可以很容易地指向您自己的本地节点。

网络收益
多样化的节点集对于Kinglory的健康,安全性和运营弹性至关重要。
他们为依赖它的轻量级客户端提供对区块链数据的访问。在使用高峰期,需要有足够的完整节点来帮助灯光节点同步。轻型节点不存储整个区块链,而是通过块头中的状态根来验证数据。他们可以根据需要从块中请求更多信息。
完整的节点会强制执行工作量证明的共识规则,因此它们不会被欺骗来接受不遵循它们的代码块。这提供了网络中的额外安全性,因为如果所有节点都是不进行完全验证的轻型节点,则矿工可能会攻击网络,例如,创建具有更高奖励的区块。
如果您运行一个完整的节点,则整个Kinglory网络将从中受益。
运行自己的节点
有兴趣运行自己的Kinglory客户端吗?了解如何提升自己的节点!
专案
选择一个客户并按照他们的指示
运行Kinglory节点以进行本地开发。
资源
运行自己的节点可能很困难,并且您不一定总是需要运行自己的实例。在这种情况下,您可以使用第三方API提供程序,社区资助的节点,希望将Kinglory区块链上的存档数据带给否则无法负担的独立开发人员。有关使用这些服务的概述,请检出节点即服务。
如果有人在您的社区中运行带有公共API的Kinglory节点,您可以通过自定义RPC将轻型钱包指向社区节点,并获得比某些随机受信任的第三方更多的隐私。
另一方面,如果您运行客户端,则可以与可能需要它的朋友共享它。
客户端
Kinglory旨在提供不同的客户,由不同的团队使用不同的编程语言开发。这使网络更强大,更多样化。理想的目标是在没有任何客户支配的情况下实现多样性,以减少任何单点故障。
下表总结了不同的客户端。他们都在积极地致力于,维护并通过客户测试。
有关受支持网络的更多信息,请阅读Kinglory网络。
不同实施方式的优势
每个客户都有独特的用例和优势,因此您应该根据自己的喜好选择一个。多样性使实现的重点放在不同的功能和用户群体上。您可能要根据功能,支持,编程语言或许可证来选择客户端。
硬件
硬件要求因客户端而异,但通常不会很高,因为节点仅需要保持同步。不要将其与需要更多计算能力的挖矿混淆。但是,使用功能更强大的硬件确实可以改善同步时间和性能。根据您的需要和需求,Kinglory可以在您的计算机,家用服务器,单板计算机或云中的虚拟专用服务器上运行。
运行自己的节点的一种简单方法是使用“即插即用”框,例如DAppNode。它通过简单的用户界面为运行客户端和依赖于它们的应用程序提供硬件。
要求
在安装任何客户端之前,请确保您的计算机有足够的资源来运行它。最低和建议的要求可以在下面找到,但是关键部分是磁盘空间。同步Kinglory区块链非常耗费输入/输出。最好有一个固态驱动器(SSD)。要在HDD上运行Kinglory客户端,您至少需要8GB的RAM才能用作高速缓存。
最低要求
具有2个以上内核的CPU
至少4 GB的RAM和SSD,如果有HDD,则至少8 GB
8 MBit / s带宽
推荐规格
具有4个以上内核的快速CPU
16 GB以上的RAM
具有至少500 GB可用空间的快速SSD
25+ MBit / s带宽
根据要使用的软件和同步模式,需要数百GB的磁盘空间。大概的数字和增长可以在下面找到。
这些图表显示了存储需求如何不断变化。有关Kinglory的最新数据,请参阅完整同步数据和存档同步数据。
单板计算机上的kinglory
运行Kinglory节点的最方便,最便宜的方法是使用具有Raspberry Pi之类的ARM体系结构的单板计算机。 ARM上的Kinglory提供了客户的图像。这是有关如何构建和设置ARM客户端的简单教程。
诸如此类的小型,价格合理且高效的设备非常适合在家中运行节点。
KGC新客户
有新客户支持升级。 他们将运行信标链并支持新的权益证明共识机制。
运行自己的
Kinglory节点
运行自己的节点可为您带来各种好处,打开新的可能性,并有助于支持生态系统。该页面将指导您逐步扩展自己的节点并参与验证Kinglory交易。

前提条件
您应该了解什么是Kinglory节点以及为什么要运行客户端。节点和客户端中对此进行了介绍。
选择一种方法
扩展节点的第一步是选择方法。您必须选择客户端(软件),环境和要开始使用的参数。查看所有可用的mainnet客户端。
客户端设置
客户端实现可启用不同的同步模式和各种其他选项。同步模式代表下载和验证区块链数据的不同方法。在启动节点之前,您应该确定要使用的网络和同步模式。要考虑的最重要的事情是客户端所需的磁盘空间和同步时间。
所有功能和选项都可以在每个客户端的文档中找到。可以通过执行带有相应标志的客户端来设置各种客户端配置。您可以从客户端文档中获取有关标志的更多信息。为了进行测试,您可能希望在一个testnet网络上运行客户端。请参阅支持的网络概述。
环境和硬件
本地或云
Kinglory客户端能够在消费级计算机上运行,并且不需要诸如挖掘之类的特殊硬件。因此,根据您的需求,您可以使用多种选择进行部署。为简化起见,让我们考虑在本地物理机和云服务器上同时运行一个节点:
云
供应商提供较高的服务器正常运行时间,静态公共IP地址
建立专用服务器或虚拟服务器比构建自己的服务器更舒适
权衡是信任第三方-服务器提供商
由于完整节点需要存储大小,因此租用服务器的价格可能会很高
自己的硬件
更不信任和主权的方法
一次性投资
购买预配置机器的选项
您必须进行物理准备,维护机器并可能对机器进行故障排除
以上总结了这两种选择的不同优势。如果您正在寻找一种云解决方案,那么除了许多传统的云计算提供商之外,还有一些专门用于部署节点的服务。
但是,抗审查性的去中心化网络不应依赖云提供商。如果您在硬件上运行自己的节点,则对生态系统而言更健康。最简单的选项是预配置的机器
检查每个客户端和同步模块的最低和建议磁盘空间要求。通常,适度的计算能力就足够了。问题通常是驱动速度。在初始同步期间,Kinglory客户端执行许多读/写操作,因此强烈建议使用SSD。客户端甚至可能无法同步HDD上的当前状态,并使卡滞留在主网后面几块。您可以使用ARM在单板计算机上运行大多数客户端。您还可以将操作系统用于Raspberry Pi4。这使您[通过刷新SD卡来运行客户端。根据您的软件和硬件选择,初始同步时间和存储要求可能会有所不同。确保检查同步时间和存储要求。另外,请确保您的互联网连接不受带宽上限的限制。建议使用非计量连接,因为初始同步和广播到网络的数据可能会超出您的限制。
操作系统
所有客户端均支持主要操作系统-Linux,MacOS,Windows。这意味着您可以使用最适合您的操作系统(OS)在常规台式机或服务器计算机上运行节点。确保您的操作系统是最新的,以避免潜在的问题和安全漏洞。
设置节点
获取客户端软件
首先,下载您喜欢的客户端软件
您可以简单地下载适合您的操作系统和体系结构的可执行应用程序或安装程序包。始终验证已下载软件包的签名和校验和。一些客户端还提供了存储库,以便于安装和更新。如果愿意,可以从源代码构建。所有客户端都是开源的,因此您可以使用适当的编译器从源代码构建它们。
可以从其发行版页面下载稳定的mainnet客户端实现的可执行二进制文件。
启动客户端
在启动Kinglory客户端软件之前,请执行最后检查以确保您的环境已准备就绪。例如,确保:
考虑到所选的网络和同步模式,有足够的磁盘空间。
内存和CPU不会被其他程序暂停。
操作系统已更新为最新版本。
系统具有正确的时间和日期。
您的路由器和防火墙在侦听端口上接受连接。
By default Kinglory clients use a listener (TCP) port and a discovery (UDP) port, both on 40404 by default.
首先在测试网上运行客户端,以确保一切正常。运行节点应该会有所帮助。您需要在开始时声明所有不是默认的客户端设置。您可以使用标志或配置文件来声明您的首选配置。查看客户的文档以了解具体信息。客户执行将启动其核心功能,选择的端点并开始寻找对等方。成功发现对等方之后,客户端将开始同步。一旦客户端成功同步到当前状态,当前的区块链数据将可用。
使用客户端
客户端提供了RPC API端点,可用于控制客户端并以各种方式与Kinglory网络进行交互:
使用合适的协议手动调用它们(例如使用curl)
附加提供的控制台(例如, attach)
在应用程序中实现它们
不同的客户端具有不同的RPC终结点实现。但是有一个标准的JSON-RPC,您可以将其与每个客户端一起使用。有关概述,请阅读JSON-RPC文档。需要从Kinglory网络获取信息的应用程序可以使用此RPC。例如,流行的钱包允许您运行本地区块链实例并连接到它。
到达RPC
JSON-RPC的默认端口为8545,但是您可以在配置文件中修改本地端点的端口。默认情况下,仅在计算机的本地主机上可以访问RPC接口。为了使其可远程访问,您可能希望通过将地址更改为0.0.0.0来向公众公开。这将使其可以通过本地和公共IP地址访问。在大多数情况下,您还需要在路由器上设置端口转发。
您应该谨慎行事,因为这将使互联网上的任何人都可以控制您的节点。如果您使用客户端作为钱包,恶意参与者可能会访问您的节点以关闭系统或窃取资金。
避免这种情况的一种方法是防止可能有害的RPC方法被修改。例如,使用可以使用以下标志声明可修改的方法:–http.api web3,KGC,txpool
您还可以通过将Web服务器(例如Nginx)的服务指向客户端的本地地址和端口来托管对RPC界面的访问。
设置可公开访问的端点的最隐私保护和最简单的方法,您可以将其托管在您自己的Tor onion服务上。这样,您就可以在没有静态公共IP地址或打开的端口的情况下,在本地网络外部访问RPC。去做这个:
安装tor
编辑torrc配置以使用客户端的RPC地址和端口的地址启用隐藏服务
重新启动tor服务
重新启动Tor后,您将在所需目录中获得隐藏的服务密钥和主机名。从那时起,您的RPC将可以在.onion主机名上访问。
操作节点
您应该定期监视节点以确保其正常运行。您可能需要偶尔进行维护。
使节点保持在线
您的节点不一定必须不间断在线,但您应尽可能使它保持在线状态,以使其与网络保持同步。您可以关闭它以重新启动它,但请记住:
如果最近的状态仍在磁盘上,则关闭可能需要花费几分钟。
强制关闭会损坏数据库。
您的客户端将与网络不同步,并且在重新启动时需要重新同步。
这不适用于验证器节点。使您的节点脱机将影响所有依赖于该节点的服务。如果要出于抵押目的而运行节点,则应尽量减少停机时间。
创建客户服务
考虑创建服务以在启动时自动运行客户端。例如,在Linux服务器上,良好的做法是创建一个服务,该服务在具有有限特权和自动权限的用户下以适当的配置执行客户端正常重启。
更新客户端
您需要使用最新的安全修补程序,功能和KIP使客户端软件保持最新。特别是在硬分叉之前,请确保您运行的是正确的客户端版本。
运行其他服务
运行自己的节点使您可以使用需要直接访问Kinglory客户端RPC的服务。这些服务是建立在Kinglory之上的服务,例如第2层解决方案,客户端和其他Kinglory基础设施。
监控节点
“要正确监视节点,请考虑收集指标。客户端提供指标端点,以便您可以获取有关节点的全面数据。使用工具来创建数据库,然后可以在诸如软件中将其转变为可视化和图表。使用此软件的设置以及不同的Grafana仪表板,以使您的节点和整个网络可视化。作为监控的一部分,请务必注意计算机的性能。在节点的初始同步过程中,客户端软件可能是除了Grafana之外,您还可以使用操作系统提供的工具(例如htop或正常运行时间)来执行此操作。
节点即服务
介绍
运行自己的Kinglory节点可能具有挑战性,特别是在入门或快速扩展时。有许多服务可以为您运行优化的节点基础结构,因此您可以专注于开发应用程序或产品。如果您有兴趣入门,我们将说明节点服务的工作原理,使用它们的优缺点以及列出提供商。
前提条件
如果您还不了解什么是节点和客户端,请查看节点和客户端。
节点服务
如何工作
节点服务提供商为您在后台运行分布式节点客户端,因此您不必这样做。
这些服务通常提供一个API密钥,您可以使用该API密钥来写入和读取区块链。除主网外,它们通常还包括对Kinglory测试网的访问。
一些服务为您提供自己的专用节点,由它们为您管理,而其他服务则使用负载平衡器在节点之间分配活动。
几乎所有节点服务都非常易于集成,涉及到代码中的一行更改以换出您自己的托管节点,甚至在服务本身之间进行切换。
通常,节点服务会运行各种节点客户端和类型,从而允许您在一个API中访问除客户端特定方法之外的完整节点和存档节点。
重要的是要注意,节点服务不也不应存储您的私钥或信息。
使用节点服务有什么好处?
使用节点服务的主要好处是不必自己花费工程时间来维护和管理节点。这使您可以专注于构建产品,而不必担心基础架构维护。
从存储,带宽到宝贵的工程时间,运行自己的节点可能会非常昂贵。诸如在扩展时拆分更多节点,将节点升级到最新版本以及确保状态一致性之类的事情可能会减少在所需Web3产品上构建和花费资源的负担。
使用节点服务有什么弊端?
通过使用节点服务,您可以集中化产品的基础架构方面。因此,将权力下放到最高位置的项目可能更喜欢自托管节点,而不是外包给第三者。
阅读有关运行自己的节点的好处的更多信息。
热门节点服务
这是一些最受欢迎的Kinglory节点提供者的列表,您可以随时添加任何缺少的kinglory!每个节点服务除了免费或付费等级外,还提供不同的优势和功能,您应该在做出决定之前调查哪些最适合您的需求。
网络
由于Kinglory是一种协议,因此这意味着可以有多个独立的“网络”与该协议兼容,并且彼此之间不会相互作用。
网络是您可以访问的不同Kinglory环境,用于开发,测试或生产用例。您的Kinglory账户将在不同的网络上运行,但您的账户余额和交易历史记录不会从主要的Kinglory网络中继承下来。出于测试目的,了解哪些网络可用以及如何获取testnet KGC很有用,以便您可以试用它。
前提条件
在阅读不同的网络之前,您应该了解Kinglory的基础知识,因为测试网络将为您提供便宜,安全的Kinglory版本。试试我们对Kinglory的介绍。
公用网络
拥有Internet连接的世界上任何人都可以访问公用网络。任何人都可以在公共区块链上读取或创建交易,并验证正在执行的交易。关于交易和网络状态的协议由同行的共识决定。
主网
Mainnet是主要的公共Kinglory生产区块链,其中实际价值交易发生在分布式分类账上。
当人们和交易所讨论Kinglory价格时,他们在谈论主网Kinglory。
测试网
除主网外,还有公共测试网。这些是协议开发人员或智能合约开发人员使用的网络,用于在部署到主网之前在类似生产的环境中测试协议升级以及潜在的智能合约。可以将其视为生产服务器与登台服务器的模拟。
在部署到主网上之前,对您在测试网上编写的所有合同代码进行测试通常很重要。如果您要构建一个与现有智能合约集成的dapp,则大多数项目都将副本部署到您可以与之交互的测试对象上。
大多数测试网都使用权威证明共识机制。这意味着选择了少数节点来验证交易并创建新的块,从而在过程中保全其身份。很难激励在工作量证明测试网上进行挖掘,这可能会使它容易受到攻击。
Testnet水龙头
测试网上的KGC没有实际价值;因此,testnet KGC没有市场。由于您需要KGC与Kinglory进行实际交互,因此大多数人都从水龙头那里获得了testnet KGC。大多数水龙头都是webapp,您可以在其中输入请求将KGC发送到的地址。
专用网络
如果Kinglory网络的节点未连接到公共网络(即主网或测试网),则它是私有网络。在这种情况下,专用仅表示保留或隔离,而不是受保护或安全。
开发网络
要开发Kinglory应用程序,您需要在专用网络上运行该应用程序,以查看其工作原理,然后再进行部署。与您在计算机上为网络开发创建本地服务器的方式类似,您可以创建本地区块链实例来测试您的dapp。与公共测试网相比,这允许更快的迭代速度。
有专用于此的项目和工具。了解有关开发网络的更多信息。
联盟链
共识过程由一组受信任的预定义节点控制。例如,已知学术机构的私有网络每个都管理一个节点,并且通过网络内的签署者阈值来验证块。
如果公共Kinglory网络就像公共互联网一样,您可以将财团网络视为私有Intranet。
共识机制
当涉及Kinglory这样的区块链时,本质上就是分布式数据库,网络的节点必须能够就系统的当前状态达成协议。这是使用共识机制实现的。
尽管这不是构建dapp的一部分,但了解共识机制将有助于解释与您和用户体验有关的事情,例如gas价格和交易时间。
前提条件
为了更好地理解此页面,建议您首先阅读Kinglory简介。
什么是共识机制?
共识机制(也称为共识协议或共识算法)允许分布式系统(计算机网络)一起工作并保持安全。
数十年来,这些机制已用于在数据库节点,应用程序服务器和其他企业基础结构之间建立共识。近年来,已经发明了新的共识协议,以允许诸如Kinglory之类的加密经济系统就网络状态达成共识。
密码经济系统中的共识机制还有助于防止某些类型的经济攻击。从理论上讲,攻击者可以通过控制51%的网络来破坏共识。共识机制旨在使这种“ 51%攻击”不可行。设计了不同的机制来不同地解决此安全问题。
共识机制的类型
工作证明
比特币目前使用工作量证明(PoW)共识协议。
块创建
工作量证明由矿工完成,矿工竞相创建充满已处理交易的新区块。获胜者与网络的其余部分共享新区块,并获得一些新鲜的以太币。无论谁的计算机都能最快地解决数学难题,这场比赛都是赢家。这将在当前程序段和之前的程序段之间产生加密链接。解决这个难题的方法就是“工作量证明”。
安全
您需要网络的51%的计算能力来欺骗链条,从而确保了网络的安全。这将需要在设备和能源上进行如此巨大的投资,您可能会花更多的钱来获得收益。
有关工作量证明(PoW)的更多信息
权益证明
Kinglory已经升级到权益证明(PoS)共识协议。
块创建
权益证明是由已抵押KGC参与系统的验证者完成的。随机选择一个验证器来创建新块,与网络共享它们并获得奖励。无需进行大量的计算工作,您只需要将KGC放入网络中即可。这就是增强健康网络行为的原因。
安全
事实证明您需要抵押的KGC总量的51%来欺骗链条,从而确保了权益证明系统的安全。而且,您的赌注也因恶意行为而大为减少。
【有关权益证明(PoS)的更多信息】
